

The Open Systems Interconnect (OSI) model is a conceptual framework that describes networking or telecommunications systems as seven layers, each with its own function.
The layers help network pros visualize what is going on within their networks and can help network managers narrow down problems (is it a physical issue or something with the application?), as well as computer programmers (when developing an application, which other layers does it need to work with?). Tech vendors selling new products will often refer to the OSI model to help customers understand which layer their products work with or whether it works “across the stack”.
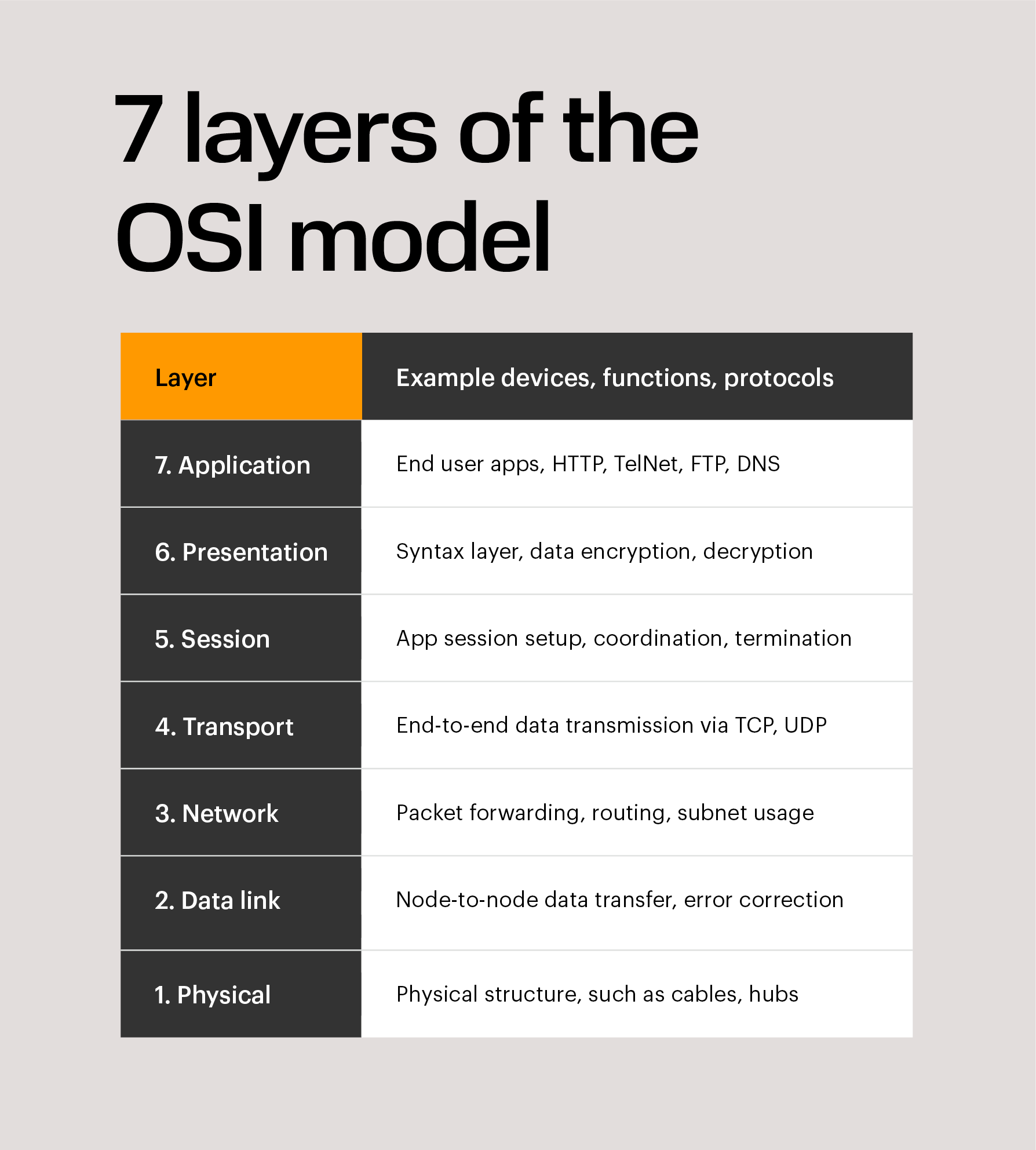
The layers (from bottom to top) are: Physical, Data Link, Network, Transport, Session, Presentation, and Application.
It wasn’t always this way. Conceived in the 1970s when computer networking was taking off, two separate models were merged in 1983 and published in 1984 to create the OSI model that most people are familiar with today. Most descriptions of the OSI model go from top to bottom, with the numbers going from Layer 7 down to Layer 1.
The layers, and what they represent, are as follows:
The Application Layer in the OSI model is the layer that is the “closest to the end user”. It receives information directly from users and displays incoming data to the user. Oddly enough, applications themselves do not reside at the application layer. Instead the layer facilitates communication through lower layers in order to establish connections with applications at the other end. Web browsers (Google Chrome, Firefox, Safari, etc.) TelNet, and FTP, are examples of communications that rely on Layer 7.
The Presentation Layer represents the area that is independent of data representation at the application layer. In general, it represents the preparation or translation of application format to network format, or from network formatting to application format. In other words, the layer “presents” data for the application or the network. A good example of this is encryption and decryption of data for secure transmission; this happens at Layer 6.
When two computers or other networked devices need to speak with one another, a session needs to be created, and this is done at the Session Layer. Functions at this layer involve setup, coordination (how long should a system wait for a response, for example) and termination between the applications at each end of the session.
The Transport Layer deals with the coordination of the data transfer between end systems and hosts. How much data to send, at what rate, where it goes, etc. The best known example of the Transport Layer is the Transmission Control Protocol (TCP), which is built on top of the Internet Protocol (IP), commonly known as TCP/IP. TCP and UDP port numbers work at Layer 4, while IP addresses work at Layer 3, the Network Layer.
Here at the Network Layer is where you’ll find most of the router functionality that most networking professionals care about and love. In its most basic sense, this layer is responsible for packet forwarding, including routing through different routers. You might know that your Boston computer wants to connect to a server in California, but there are millions of different paths to take. Routers at this layer help do this efficiently.
The Data Link Layer provides node-to-node data transfer (between two directly connected nodes), and also handles error correction from the physical layer. Two sublayers exist here as well–the Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. In the networking world, most switches operate at Layer 2. But it’s not that simple. Some switches also operate at Layer 3 in order to support virtual LANs that may span more than one switch subnet, which requires routing capabilities.
At the bottom of our OSI model we have the Physical Layer, which represents the electrical and physical representation of the system. This can include everything from the cable type, radio frequency link (as in a Wi-Fi network), as well as the layout of pins, voltages, and other physical requirements. When a networking problem occurs, many networking pros go right to the physical layer to check that all of the cables are properly connected and that the power plug hasn’t been pulled from the router, switch or computer, for example.
Most people in IT will likely need to know about the different layers when they’re going for their certifications, much like a civics student needs to learn about the three branches of the US government. After that, you hear about the OSI model when vendors are making pitches about which layers their products work with.
In a Quora post asking about the purpose of the OSI model, Vikram Kumar answered this way: “The purpose of the OSI reference model is to guide vendors and developers so the digital communication products and software programs they create will interoperate, and to facilitate clear comparisons among communications tools.”
While some people may argue that the OSI model is obsolete (due to its conceptual nature) and less important than the four layers of the TCP/IP model, Kumar says that “it is difficult to read about networking technology today without seeing references to the OSI model and its layers, because the model’s structure helps to frame discussions of protocols and contrast various technologies.”
If you can understand the OSI model and its layers, you can also then understand which protocols and devices can interoperate with each other when new technologies are developed and explained.
In a post on GeeksforGeeks, contributor Vabhav Bilotia argues several reasons why the OSI model remains relevant, especially when it comes to security and determining where technical risks and vulnerabilities may exist.
For example, by understanding the different layers, enterprise security teams can identify and classify physical access, where the data is sitting, and provide an inventory of the applications that employees use to access data and resources.
“Knowing where the majority of your company’s data is held, whether on-premises or in cloud services, will help define your information security policy,” writes Bilotia. “You can invest in the correct solutions that provide you data visibility within the proper OSI layers once you have this knowledge.”
In addition, the OSI model can be used to understand cloud infrastructure migrations, particularly when it comes to securing data within the cloud.
And because the model has been around for so long and understood by so many, the uniform vocabulary and terms helps networking professionals understand quickly about the components of the networking system “While this paradigm is not directly implemented in today’s TCP/IP networks, it is a useful conceptual model for relating multiple technologies to one another and implementing the appropriate technology in the appropriate way,” Bilotia writes. We couldn’t agree more.
If you need to memorize the layers for a college or certification test, here are a few sentences to help remember them in order. The first letter of each word is the same as the first letter an OSI layer.
From Application to Physical (Layer 7 to Layer 1):
From Physical to Application (Layer 1 to Layer 7):